Healthcare Breach Report analysis from the OCR/HHS
Posted on Mon 19 August 2024 in Thought
Breach Report!
Why am I writing about healthcare breach reports? Well I like data, especially unsexy data. Also a couple friends (you might know who) and I are looking into some unsexy parts of industries that are underserved and in need of help to make impact for the better good.
My Experience in Healthcare Tech
Some may know I use to work for a healthcare tech company. I had a great time working there amongst friends and the founders. Being submerged into the murky depths of what America calls healthcare was a pitful joke. But even more of a joke, is seeing the number of breaches increase year after year especially in the healthcare sector. The most recent known breach(non healthcare) was the National Public Data breach. Guess what that breach data contained? Personal data, that could be used to impersonate an individual and gain further access to their life's treasures including medical history.
I am sure this was your reaction:

Rather than using fearmongering tactics to scold individuals, it's best to try to understand why these events happen.
Focusing on the HHS Reports
This is why I wanted to take a look at Reports to Congress on Breach Notification Program. The high level, is that the HITECH Act requires the U.S. Department of Health and Human Services (HHS) to submit an annual report to Congress about data breaches in healthcare. The reports include:
- The number of breaches
- What caused them
- How HHS responded
- It also needs to be made available to the public on the HHS website
The reports themselves split up the data about the above bullet points but in true fashion arent sexy and also really needs to be surfaced more broadly.
Diving Into the 2022 Report
I focus on the most "recent" available report from 2022 since 2023 is not available....and ill introduce a data viz app my friends and I quickly collabed on to convey what has been seen over the last 29 months based on data from the OCR breach report investigation portal.
Hint, you can do analysis on publicly recieved breaches from 2023 and also 2024 data breaches to generate similar reports but sexier graphs before HHS reports are available. Also your empowered to conduct your own analysis based on your specific interests.
Report Insights Gleaned
Key Statistics from the 2022 Report
First, off the bat, the summary speaks of:
- 3% increase of breaches since their 2021 report (607 to 627)
- 41 Million individuals impacted (32 million caused by Hacking)
- The number one causes of breaches... Hacking... by location (vector) being network servers (I got thoughts...)
- OCR investigated all 626 breaches but completed 799? (some from previous year 2020...check their footnotes, pg 8)
- There was some monetary pay out for some investigation that was low and from 3 closed investigations
For me, a breach is a breach, may it be back hacking or mistaken unauthorized access. Their definition is "the acquisition, access, use, or disclosure of PHI in a manner not permitted by [the HIPAA Privacy Rule] which compromises the security or privacy of the PHI." However, the detailed reports often categorize the data based on whether the affected entity had more than 500 individuals impacted or fewer than 500.
Below, I found the percentage of changes in breaches particularly interesting—not so much in terms of volume, but in the context of 'high-quality' data breaches concerning sensitive information. As we know, more data doesn’t always equate to better quality (or devestating in this case), and I believe the same principle applies to breaches. 🤷
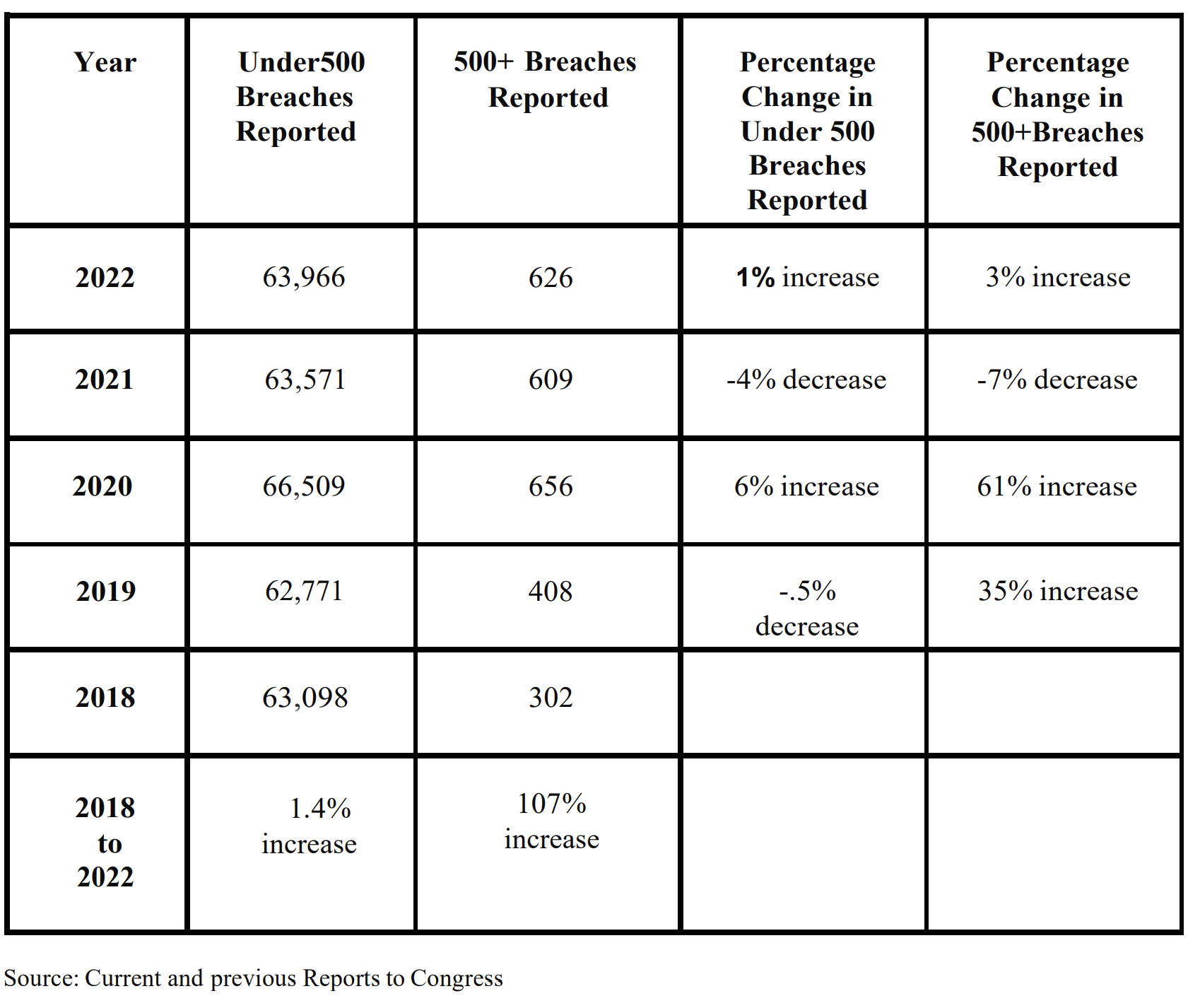
Important note: the OCR portal only shows data for breaches affecting more than 500 individuals

Deeper Dive into Network Server Breach location
When analyzing more of the 2022 report, I was interested in what "Network Servers" meant as it was one of the main vectors of "Hacking/IT" breaches. And my friend suggested they potentially use network server very liberally to include SaaS applications but could still include laptop, ftp servers etc.

As HHS highlights, ransomware plays a significant role in compromising network servers. However, it raises the question of what the initial attack vector was—potentially something like phishing or malware. Unfortunately, the OCR portal limits showing entities with one type of breach and one location, even when multiple may be involved/selected.
The Need for Greater Specificity
It could also better serve if "Hacking/IT Incident" and "Network Server" were further broken down into more specific categories. As they stand, these broad classifications can obscure important details about the nature of the breaches. For example, distinguishing between different types of servers, such as web servers versus file servers versus an S3 bucket, or identifying the specific methods used in the initial compromise, could provide deeper insights and more targeted remediation strategies.
By breaking down these categories, we could gain a clearer understanding of how these breaches occur, enabling more precise and effective countermeasures. This level of detail is crucial, especially as the healthcare industry continues to be a ripe target for cyberattacks.
Evaluating Remediation Efforts
The 'Remedial Action Reported' section highlighted what I perceived as some of the weaker remediation efforts following the breaches. Measures like implementing MFA, training staff, and adopting encryption seemed more like partial fixes rather than comprehensive solutions that drive continuous, meaningful change. Below are the specific remediations listed:
- Implementing multi-factor authentication for remote access;
- Revising policies and procedures;
- Training or retraining workforce members who handle PHI;
- Providing free credit monitoring and identity theft protection services to customers;
- Adopting encryption technologies;
- Imposing sanctions on workforce members who violated policies and procedures for removing PHI from facilities or who improperly accessed PHI;
- Changing passwords;
- Performing a new risk analysis; and
- Revising business associate contracts to include more detailed provisions for the protection of health information.
The Challenge for Smaller Healthcare Providers
I also wonder (know to some extent) how many of these entities have dedicated IT, Security, or GRC (Compliance) staff to effectively implement these remediations, especially when things can be automated where possible. A lot of responsibilities fall on the cover entities without IT or security resources. Not all healthcare providers or entities can have the resources of a Kaiser Permanente...
We can not forget about the SMBs of healthcare, they power our system.
It's also important to note that the number of breaches affecting fewer than 500 individuals is significantly higher than those impacting larger groups. This could be a classic "death by a thousand cuts" scenario, where the cumulative effect of these smaller breaches is just as devastating as a single massive breach. These smaller incidents shouldn't be ignored—they can collectively cause substantial harm and, in many ways, represent an equally critical threat to the healthcare ecosystem.
Lessons Learned submitted to the OCR
Key Deficiencies Highlighted in the 2022 Report
The 2022 breach report highlights several key deficiencies (in more details compared to previous years) in how healthcare entities protect ePHI/EHR. Key areas needing improvement include:
-
Security Management Process: Many entities failed to conduct comprehensive risk analyses, often overlooking crucial areas where PHI is stored or transmitted. This incomplete assessment left them vulnerable to breaches. Additionally, entities were found to repeatedly ignore the implementation of effective risk management measures, which would reduce known vulnerabilities.
-
Information System Activity Review: The investigations revealed that many entities either lacked regular reviews of system activity or conducted them in a limited and reactive manner. Without proper monitoring, suspicious activity could go undetected, increasing the risk of breaches.
-
Audit Controls: A significant number of entities did not have proper mechanisms in place to record and examine system activities, limiting their ability to detect and respond to suspicious actions. In some cases, logs were not maintained long enough to be useful in security incident investigations.
-
Response and Reporting: Many entities had inadequate or non-existent processes for responding to and reporting security incidents. This failure to act promptly can prolong the effects of security breaches and potentially allow future incidents to occur.
-
Person or Entity Authentication: Weak authentication procedures, such as poor password practices and the sharing of credentials, were common issues. Strong authentication is crucial in preventing unauthorized access and safeguarding ePHI from cyber-attacks.
A Differentiated Perspective
Opportunities in the Healthcare Space
Given these deficiencies, I see significant white space opportunities for innovative product development, particularly in Security Management Processes and Information System Activity Reviews. While these categories may go by different standardized names in cybersecurity, this presents a chance to create something truly differentiated in an area with few or no established players in the healthcare space.
Rethinking Breach Causes
Also noting that if you are reading the reports and the news, you do see high profile breaches related to hacking or ransomware. Although majority of the breaches in these reports do not make the main stream news, it does suggest something different. From our conversations with healthcare providers and cover entities, there are several points of issues leading to breaches...and some may not be what you may consider a breach. Examples including
- Deidentified data problems
- Manual processes done by humans
- Patient attribution
And this is just to name a few, as these issues are more common than ransomware. Remember how I stated earlier its about the quality and not quanity of data...
If we are to uplevel the underserved industries, we should focus on creating a truly differentiated outcome, not just a marginally better one.
Ooh, Yeah, Our Breach Report Data Viz App
Given that HHS/OCR has not yet published their 2023 report at the time of this writing, we decided to release a small extensible app that leverages the existing data they have made available. This allows individuals to generate their own insights and analyses without having to wait for the official reports.
The app provides key features like customizable data visualizations, filtering by year, state, and breach type, and the ability to explore trends and patterns. Additionally, it integrates with Datasette, enabling more advanced querying and in-depth exploration of the dataset. This empowers users to dig into the data, uncover insights, and make informed assumptions well ahead of the release of new reports. Below are a couple screenshot including one that doesnt exist in the annual breach report.
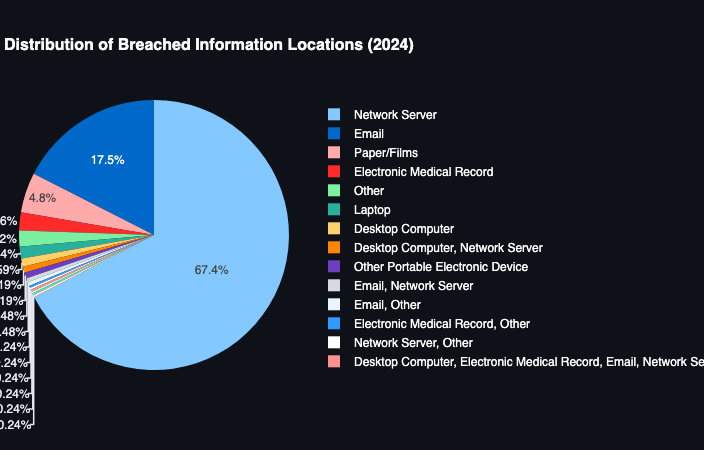
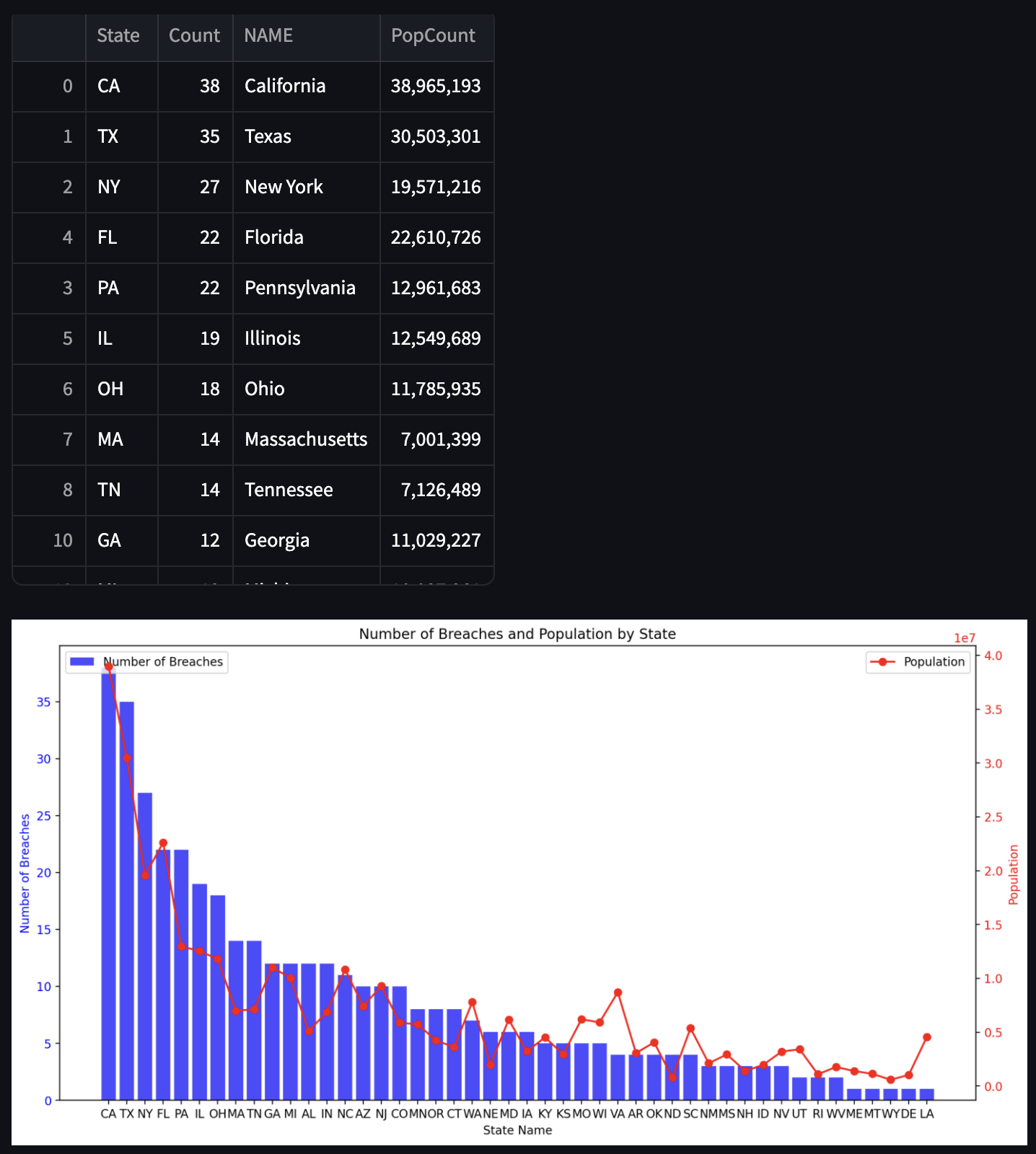
To get the full feature, you can download the app from github