macOS VM prep on Apple Silicon [2024-02-19]
Posted on Mon 19 February 2024 in Thought
macOS setup on silicon
Setting up virtual machines (VM) has always been fun for me, yet it seems to be a practice from the past. When setting up a VM of macOS Sonoma on Apple Silicon, particularly the Apple M1 Max with 64GB of memory, I was in search of modern guides. I aimed to set up my environments in a secure manner, to mitigate worries about executing malware/exploits that could escape from VM to host, or simply to be able to revert my VM back to a stable state. What I found was a guide from SentinelOne which is decent but dates back to spring 2019. Therefore, I decided to create my own rendition and update here for those who might need a pointer in the right direction. In this post I use Parallels Desktop 19 for Mac Pro Edition.
macOS VM parallel limitations
For starters, Parallels definitely makes it easy to install macOS as a VM, but it does include some limitations when configuring the host. With Debian, Ubuntu, and other Linux distributions, they seem to offer a pretty easy way to configure the guest VM from the control center. For macOS, Parallels's CLI, prlctl, will be your friend. For a list of available commands, check out Parallels Desktop for Mac.
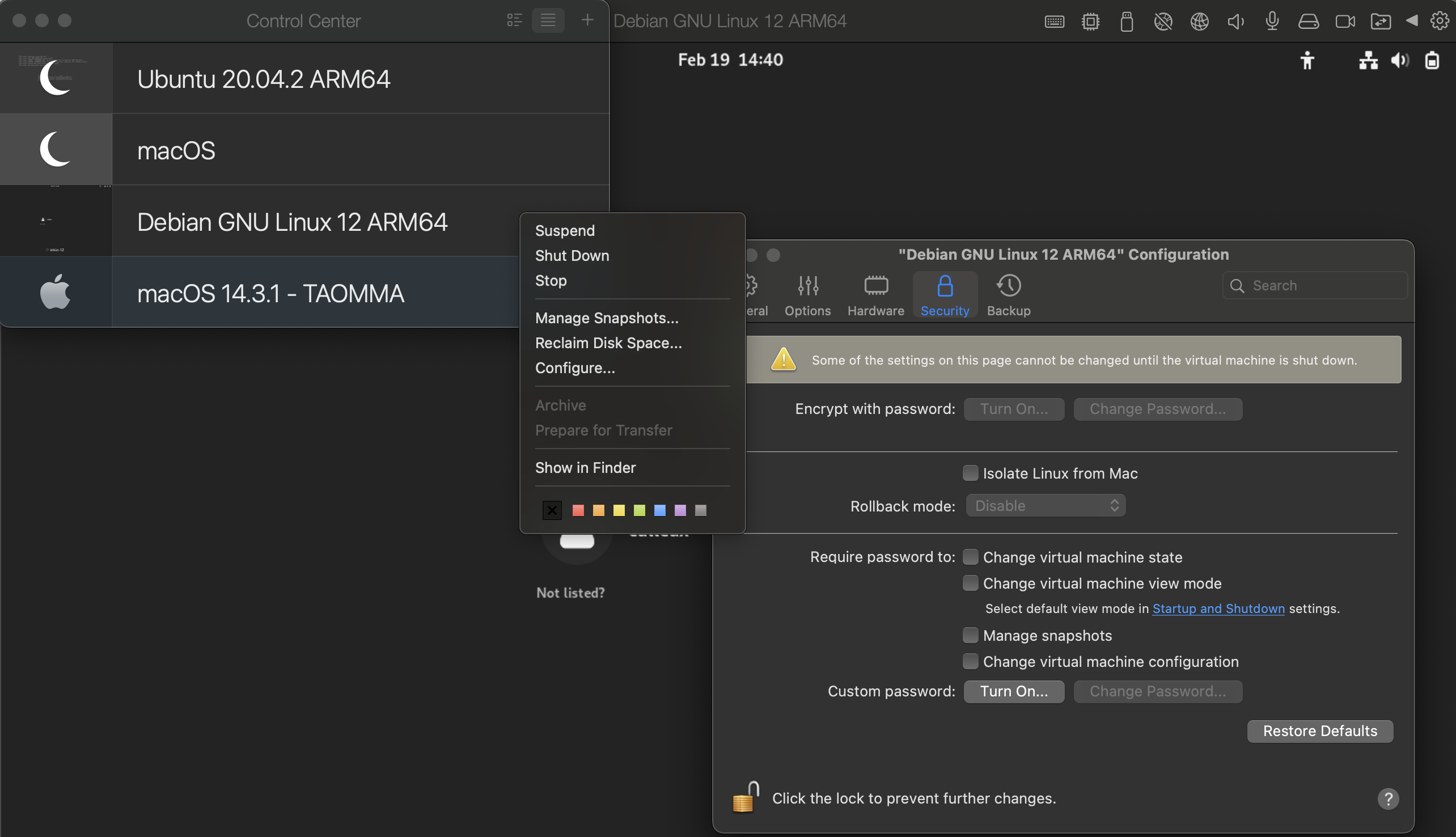
debian config screen
non-existent macOS config screen
Straight to the commands
Below is a set of commands I used to secure my VM for exploit development and malware analysis. Feel free to pick and choose what suits you. Note that the VM needs to be in a stopped state; otherwise, you will encounter a failed applied settings message like below:
Failed to apply settings: This virtual machine is suspended. To be able to edit the configuration of this virtual machine, you need to stop it.
This changes the name of the VM from "macOS (1)" (a duplicated/current name) to "macOS 14.3.1 - TAOMMA":
prlctl set "macOS (1)" --name "macOS 14.3.1 - TAOMMA"
Change memory size:
prlctl set "macOS 14.3.1 - TAOMMA" --memsize 8192
Change MAC address:
You only really need to change the first 3 bytes. This helps with anti-debugging techniques that malware sometimes deploy to see if they are being examined. This must happen when the VM is in a stopped state:
prlctl set "macOS 14.3.1" --device-set net0 --mac 123456789ABC
Disable sharing the host machine's folders and files.
As convenient as this is, I would rather not have any potentially malicious code surfing my host machine files:
prlctl set "macOS 14.3.1 - TAOMMA" --shf-host-defined off
Disable auto-share camera:
prlctl set "macOS 14.3.1 - TAOMMA" --auto-share-camera off
Isolate the virtual machine from the host:
prlctl set "macOS 14.3.1 - TAOMMA" --isolate-vm on
Alternatively...
Although I ran these commands via the CLI, you could also update the config.pvs file in the "/Users/username/Parallels/virtual machine name" directory. It has some other more technical configurations that might be of use for setting up. Remember, you can only modify this file with the VM in a powered-off/stop status.
Example Disabling Clipboard Sync and Drag-Drop Features
<ClipboardSync dyn_lists="" Enabled_patch="1">
<Enabled>0</Enabled>
<PreserveTextFormatting>1</PreserveTextFormatting>
</ClipboardSync>
<DragAndDrop dyn_lists="" Enabled_patch="1">
<Enabled>0</Enabled>
</DragAndDrop>
Wrapping this up, navigating the complexities of setting up a macOS VM on Apple Silicon can be a annoying task, especially when looking for up-to-date guides. Through this post, I've shared some of the configurations that have helped me create a secure environment for my development and analysis work. Whether you're diving into malware analysis or just looking for a safe sandbox for testing, these tips should provide a solid starting point. As with any security measures, it's always a good practice to stay informed about new vulnerabilities and update your strategies accordingly.